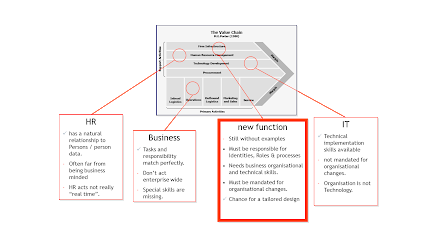


When we try to define the term "digital transformation", we encounter such exciting explanations as "Digital transformation marks a radical rethinking of how an organization uses technology, people and processes to radically change business performance". (George Westerman, MIT Principal Research Scientist and author in Leading Digital: Turning Technology Into Business Transformation).
Frequently, no less is required than reinventing the business and finding new sources of revenue.

Will one day a superintelligence assign us the status we have reserved for wildlife theses days?
There is no consensus at all. There are statements, beliefs, positions, no proof. So, whom to believe?
And all men kill the thing they love,
By all let this be heard,
Some do it with a bitter look,
Some with a flattering word,
The coward does it with a kiss,
The brave man with a sword!
Oscar Wilde,
Ballad of Reading Gaol,1898

Recently I joined a colleague for an after work beer to one of Düsseldorf’s oldest and most rustic Altbier (literally “old beer”) taverns.
Quickly, we had engaged in a profound discussion about the nature of artificial intelligence and its effects on our lives and the world as such in general.
We were not the only ones reflecting their professional and beyond thoughts in a more convenient and inspiring atmosphere than a noisy crowded open space office with only with castrated and amputated computers at hand.

Dr. Horst Walther ist als neuer Prinzipal in das Diplomatic Council Otto Schell Institute for Digital Transformation (DCOS Institute) eingetreten. Er verantwortet dort neben dem Namensgeber Otto Schell den Aufbau eines weltweiten Netzwerks von Digitalisierungsexperten. Das DCOS Institute hat sich zur Aufgabe gemacht, im Zusammenwirken mit den Vereinten Nationen (UNO) die Auswirkungen der Digitalisierung auf Politik, Wirtschaft und Gesellschaft gleichermaßen wissenschaftlich und praxisnah zu begleiten. Das Diplomatic Council (DC) ist ein globaler Think Tank und Business Network mit Beraterstatus bei der UNO.

Vietnam verzeichnet derzeit ein starkes Wachstum in der IT-Branche, was Schweizer KMU einen neuen Markt bietet und neue Möglichkeiten der Zusammenarbeit eröffnet. Besonders gut ist die Entwicklung im Bereich der Telekommunikationsinfrastruktur, in der Hardware- und Softwareindustrie, im Sektor für digitale Inhalte sowie im IT-Personalwesen

At first sight nothing – you would say, except perhaps that both of them, the General Data Protections Regulation and the change imperative digital transformation, are currently hot topics in the public professional debate. And I would even agree – at least at first sight.
On the role of modelling and simulation as an integral part of any digital transformation
In my earlier days, when I was advocating the use of roles, or their dynamic equivalents, business rules (in combination with business attributes), I once ran into an enlightening discussion.
In an experts panels on an Identity conference I heard one of the experts state: "What sense does role modelling make, if, whenever we complete an organisations role model and are about to implement it, the organisation has changes considerably meanwhile.

And they have to do so at the pace of technology – not at the traditional banking pace.
This sounds provocative. And the legitimate question arises, if I do believe in it myself.
Well, it is an extreme position. Usually I am not advocating extreme positions. Life is colourful and multi-facetted. In reality you most often neither climb the steep slope on the right, nor on the left, but take some middle ground. But experience also tells us, that success is by no means guarantied, when you just conveniently follow a tradition.

But you Tiresias, blind old man, perceived the scene, and foretold the rest¹.
McKinsey, well established Consultancy for those for those who don't shy away from high prices for at times good value, did it again: Capturing the Zeitgeist in one of their recent surveys about automation.
A light-hearted view at some idiosyncrasies of naming processes in Identity & Access
A few of you may know that process definition in general and Identity & Access processes in particular are the special object of study for me since several years already. As a tiny indication how serious I took this self-imposed duty the formation of the standardisation initiative GenericIAM.org may be taken.
During a long professional career a lot is supposed to happen along the intricate windings of our mortal life and hence some folklore piles up to be drawn from when telling our grandchildren our adventures.
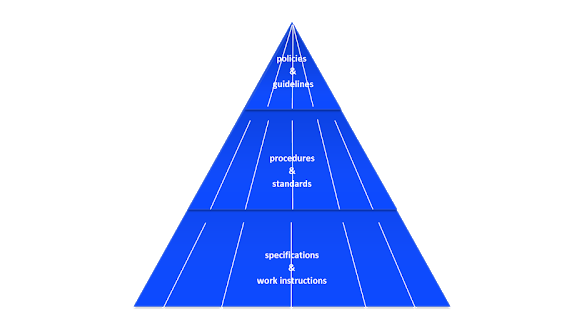
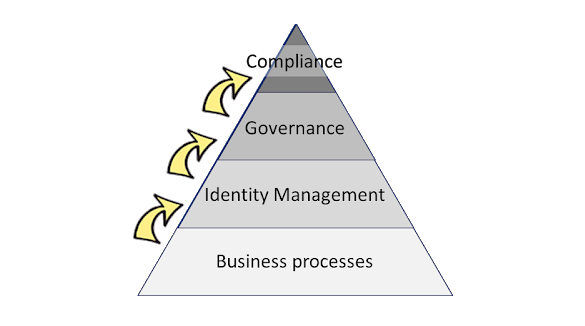
In last weeks contribution (Identity & Access Governance in the age of digital transformation) I was outlining the general picture, answering the question, what Governance is after all, what it means, when applied to Identity & Access, emphasizing the need to look at Identity and Access separately, and finally breaking ’direction' down, following the downstream path from strategy to executable rules. Today I will cope with how to make policies & guidelines actionable.
Identity & Access Governance obviously is a difficult task. Many major corporations struggle to meet their various compliance criteria, which could be expected as a natural by-product of good governance. But having hardly completed this job, the next one, innocently called “digital transformation” knocks at the door.
In last week's contribution (From ‘oversight’ to the algorithm-driven company) I contemplated about the necessary underpinnings of a digital transformed corporation, gave some justification why it is so hard to answer the obviously simple question, which is at the core of any oversight: Who has (had) access to which Resources? And I mentioned how oversight is executed according to the state-of–the-art. In this third and final post I will discuss current trends and - with the help of professional analysts - try to look ahead.
In the field of Identity- & Access Management terms like authentication an authorisation are well understood, frequently used and everyone knows what they mean. Really?
We saw that maintenance of roles is rather simple (How to find roles). Maintenance just consists of the CRUD (create, read, update & delete) operation on the role object. But what if a role is in use somewhere already? In this case obviously the referential integrity has to be maintained. Database people may be familiar with this requirement. But, can it be changed at all? Do we need to renew all approvals we received while assigning this role to an identity? Can it be done within the regular attestation?
7+1 reasons and more to expect
There are several caveats to be aware of up front when starting a major IAM project. These useful hints are driven by experience from projects that went wrong due to some common misconceptions:
You might remember my simple model of static objects of the corporation. Now here comes the complexity. In my nice a lean model of the static IAM objects there was one innocent and less impressive object called constraint.
I borrowed the term constraint from RBAC [1], where various kinds of constraints can be specified. RBAC knows separation of duty constrains, prerequisiteconstraints, and cardinality constraints. The constraints of the RBAC model are expressed using the Object constraint Language (OCL). OCL constraints, based on first-order logic, are generally perceived as being difficult to understand.

This post will be essentially in German as it deals with some German language idiosyncrasies. Although I have the strong and irrefutable impression, that we do have this cognitive dissonance in the English language universe as well I would like to leave it to a more competent person to comment on the confusing use of the word competence

Not, many of you may have read this Blog post before here, posted at Sat. June 30thto the GenericIAM Blog. Here I made the statement that "Roles are the organization". You may read through this short contribution before you go on listening to me.

Das neue mittelstandsgerechte Konzept „preisgünstiger, praktischer und auf Deutsch“ hat sich als erfolgreich erweisen und eine kleine aber sehr engagierte Gruppe angesprochen.
Der überwiegende Teil der Beiträge wurde von Anwendern für Anwender vorgetragen. Darunter waren Stadtwerke München, P3 Ingenieurgesellschaft, Berliner Stadtreinigung, AMAG Austria Metall AG, Kassenärztliche Vereinigung Bayerns, Henkel AG & Co. KGaA und SAP Deutschland.
Inhaltlich befassten sich die Beiträge mit Themen rund um IAM (Identity- & Access Managment), GRC (Governance, Risk & Compliance), DLP (Data Leak Prevention) und Cloud Computing.

Just recently the Gartner group reported shrinking IT security budgets – by 3 – 6%. Only identity Management makes an exception. Identity Management – or, let’s be a bit more specific: Identity- & Access Management (IAM) - part of IT security? Hmmm …

Identity- & Access Management (IAM) quite often is regarded as just another part of information security management (ISM).
Information Security management in turn often suffers from its not totally positive reputation. Well, everybody agrees that some level of Information Security seems to be necessary after all. But on the other hand we have to carry the heavy burden of high cost and key person effort. Most often no one in the corporation is able to prove with reasonable certainty to what degree it contributes to the corporate success. On the other hand everyone can feel in his daily life that strict security measures slow down the affected activities and introduce inconveniences. Moreover vendors in the Information security arena tend to sell their products via the fear factor – putting unsavoury pressure on the top management

Shocked by the fact, that u to 80% of all effort in IAM implementation projects has to be buried in process definitions we had the honorable idea to collect all those experiences and assemble a generic process model. Based on this generic IAM model (hence our brand became GenericIAM) most future modeling attempts should turn out to be much easier and hence cheaper.